HOW MUCH CYBERSECURITY IS ENOUGH?
Boards and senior executives do not have the needed visibility into their cybersecurity program leaving them legally exposed and uniformed in the decision-making process.
Traditional approaches such as third-party assessments, IRM/GRC tools, and self assessments do not address the legal requirements to mitigate the risk associated with the tort of negligence in the event of a cybersecurity incident.
ADDRESSING THE REAL CHALLENGES OF CYBERSECURITY PROGRAM PERFORMANCE
With Context
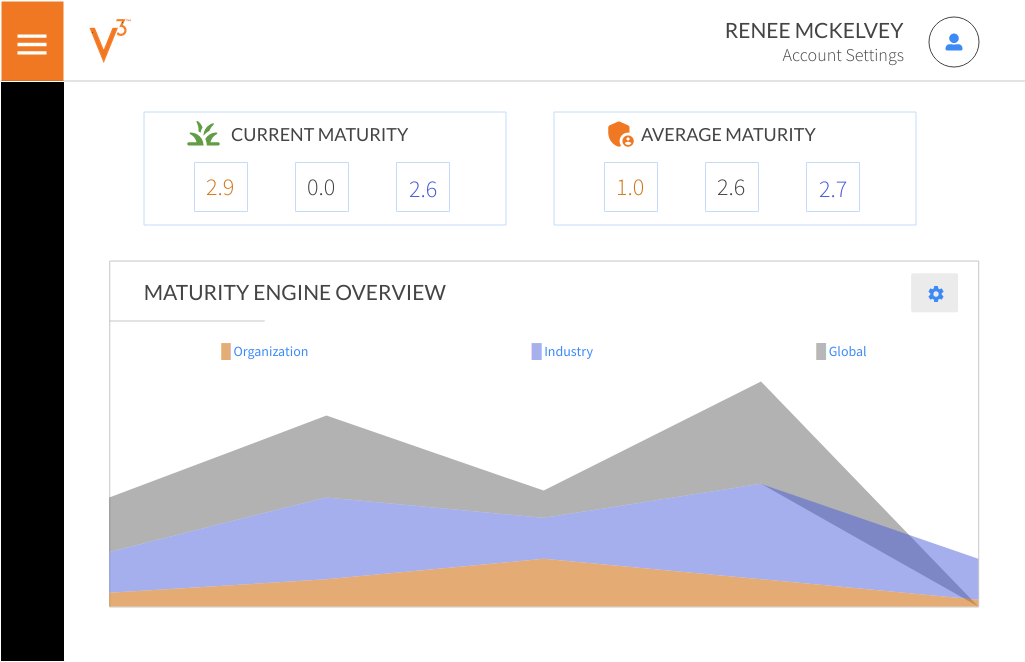
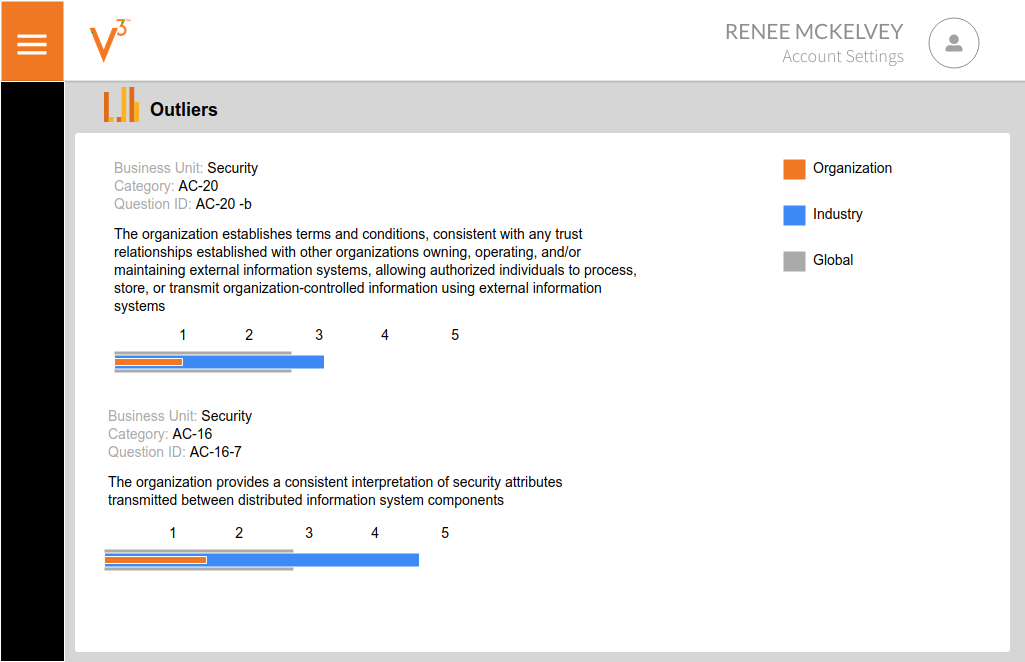
The ability to provide business context and show fiscal alignment with cyber risk is no longer out of reach. The Minerva platform provides business-related benchmarking in order to provide executive-level reports with business context. Draw from the community of cyber leaders and set yourself apart by being able to discuss the business context of your security program. Ensure that your business is maximizing its core business.
Through Communication
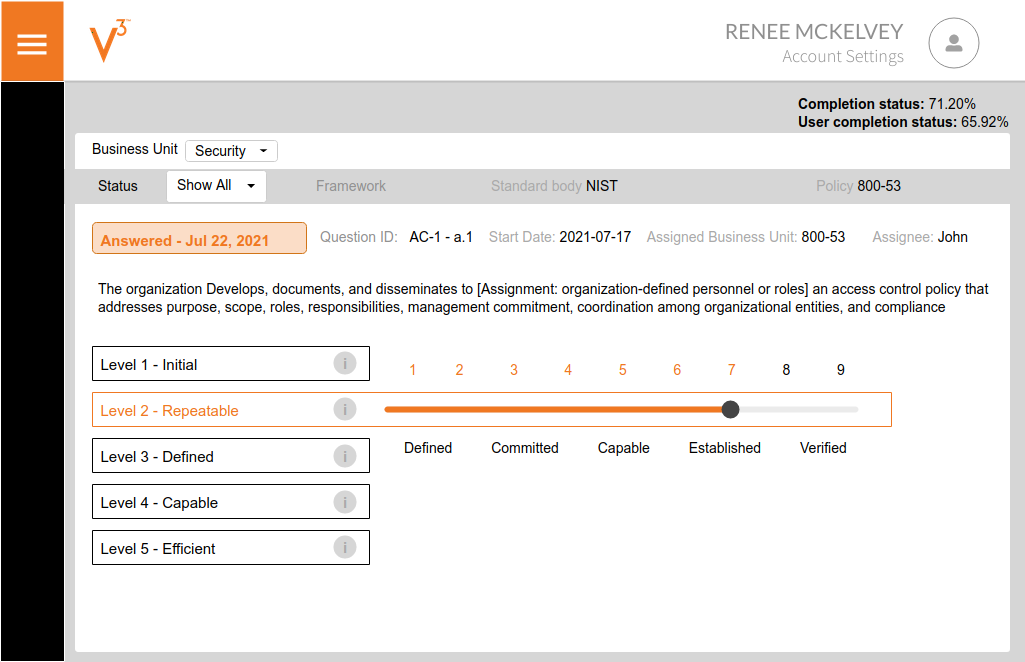
The ability to provide real-time data to inform business decisions in a form that business leaders can understand will differentiate you as a cyber leader. Remove the complexity of the cyber program and provide your stakeholders easy to understand data using visualization and world-recognized data.
Driving Culture
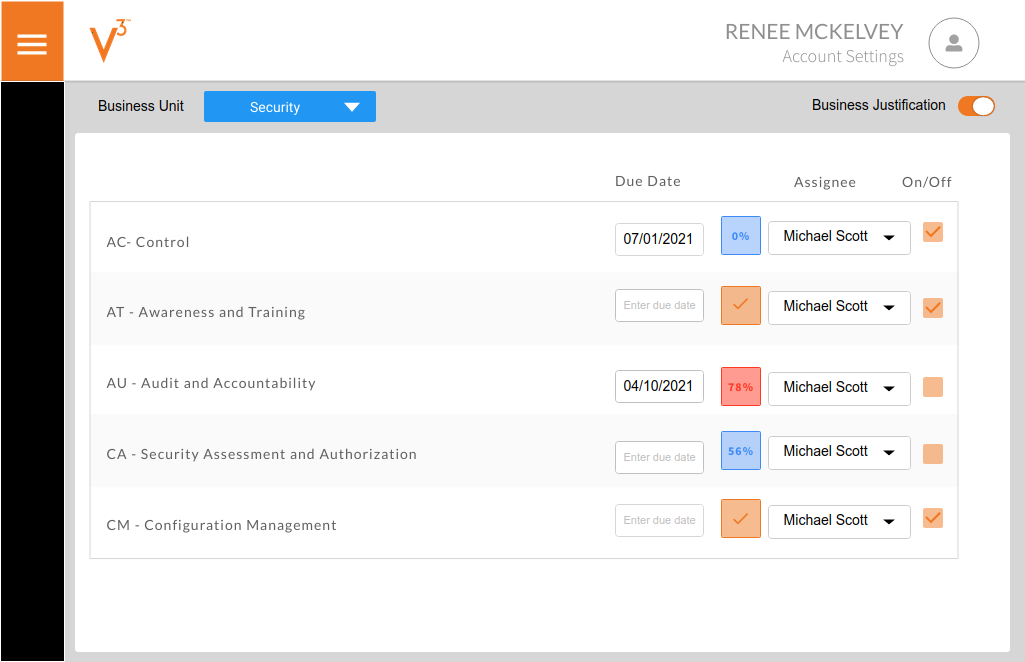
Developing a security culture is not something that just happens. It is something that requires strong leadership but also requires the ability to drive clear lines of responsibility throughout the organization. The ability to line areas of responsibility with control ownership has challenged security programs for years, but those times are history. Establish your responsibility hierarchy and help drive a security culture with technology.
Balancing Business Needs and Risks
The ability to drive cybersecurity decisions based on data, and not emotion, allows leaders to gain credibility across the organization. The ability to communicate the financial decisions associated with your cybersecurity program by targeting organizational and personal exposure improves program support while improving team confidence. The Minerva platform is the only platform in the world that provides a data-driven intelligence-based approach to cybersecurity roadmap development.