The Minerva Difference: Clarity You Can Defend
Minerva was built to change that — by transforming cyber risk from technical noise into a clear, defensible, and continuously improving management discipline.
Why Traditional Approaches Fall Short
Point-in-time assessments, compliance-driven tooling, and labor-intensive consulting approaches degrade quickly as conditions change. Visibility fades, priorities drift, and leaders are left making high-stakes decisions without a clear, defensible foundation.
The result is fragmented insight, misaligned investment, and increased exposure when scrutiny arrives.
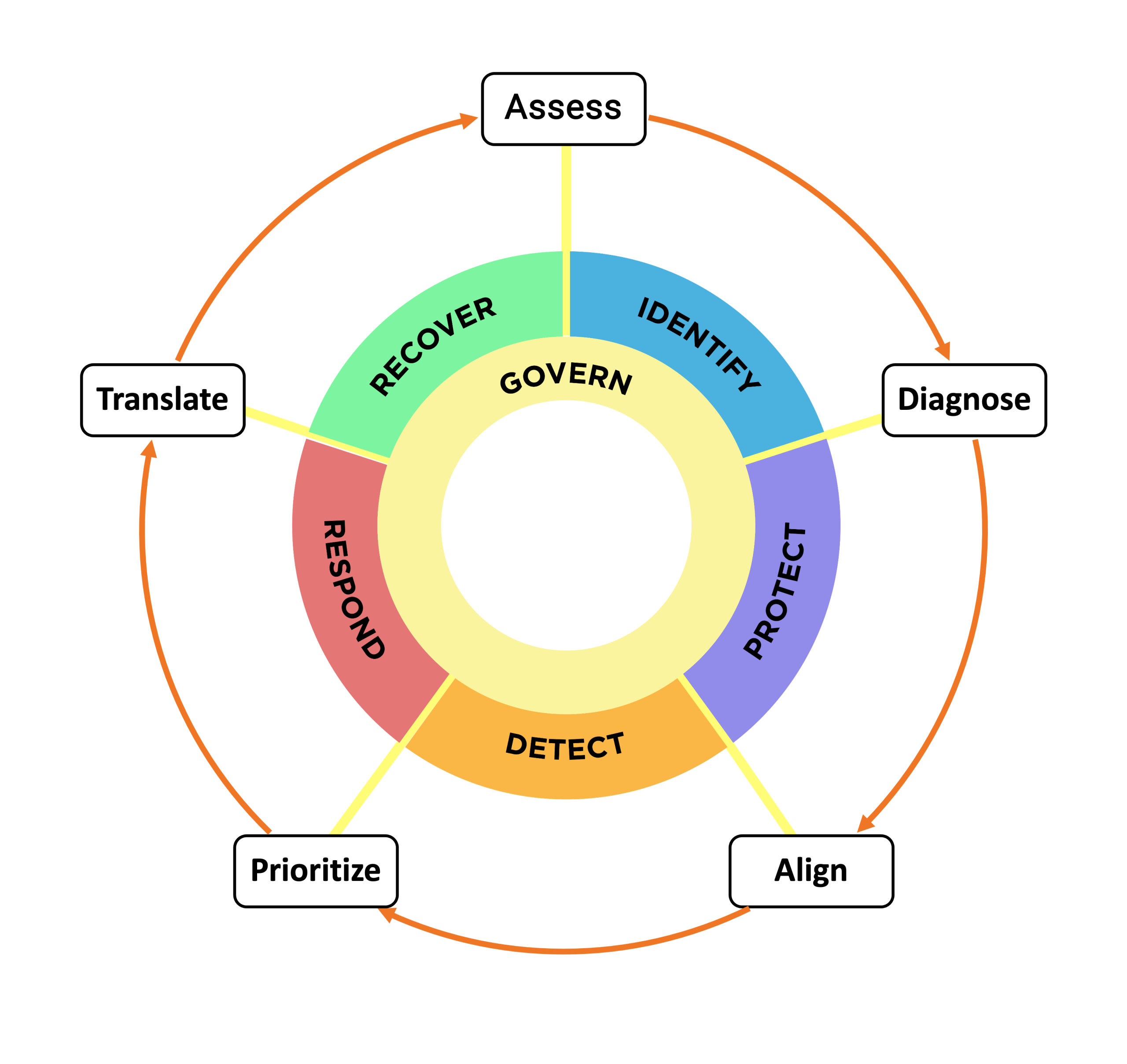
A Different Starting Point: The ADAPT™ Risk Model
ADAPT™ reflects how cyber risk actually behaves inside organizations:
Assess — establish an objective baseline
Diagnose — identify the conditions driving risk
Align — connect requirements, resources, and accountability
Prioritize — sequence actions for maximum impact
Translate — make risk understandable and actionable for leadership
ADAPT™ creates a shared language between technical teams and leadership — reducing uncertainty, improving confidence, and enabling defensible decisions over time.
How Minerva Operationalizes ADAPT™
Rather than static assessments or disconnected tools, Minerva™ provides continuous visibility across people, process, and technology — aligned to established frameworks and regulatory contexts.
Organizations use Minerva™ to:
- Maintain a living risk baseline
- Understand maturity and progress over time
- Identify both acute and systemic risk drivers
- Translate cyber complexity into leadership-ready insight
This is how risk management becomes sustainable — not episodic.
Minerva enables organizations to perform comprehensive assessments aligned to recognized frameworks and regulatory contexts — not as a one-time exercise, but as a living baseline that reflects real operating conditions across people, process, and technology.
How Minerva™ Operationalizes Assess
- Conducts structured assessments aligned to industry frameworks and sector-specific requirements
- Centralizes evidence, documentation, and artifacts in a single system of record
- Maintains a dynamic risk register that surfaces gaps often invisible at the leadership level
- Assigns controls and responsibilities in a way that reflects how work actually happens
Why This Matters
Minerva analyzes control performance, maturity, and context to reveal whether risk stems from operational capability gaps, governance weaknesses, workflow breakdowns, or systemic conditions — not just missing controls.
How Minerva™ Operationalizes Diagnose
- Benchmarks organizational maturity against peer and industry data
- Analyzes control-level performance to identify patterns and systemic weaknesses
- Distinguishes isolated issues from underlying conditions that drive repeated risk
- Surfaces the most consequential risks based on impact and exposure
Why This Matters
Minerva brings structure to how risk is owned, approved, and addressed — aligning security, IT, operations, and leadership around a shared understanding of responsibility and execution.
How Minerva™ Operationalizes Align
- Defines clear risk ownership and authorization paths across technical and non-technical teams
- Aligns cybersecurity activities with existing workflows and operational processes
- Consolidates evidence, artifacts, and approvals into a unified system of record
- Reduces duplicated effort and friction as teams, tools, and priorities evolve
Why This Matters
Minerva helps organizations sequence cybersecurity initiatives based on real-world risk, organizational readiness, and expected impact, ensuring limited resources are applied where they deliver the greatest measurable reduction in exposure.
How Minerva™ Operationalizes Prioritize
- Evaluates initiatives based on risk reduction, impact, cost, and operational effort
- Models tradeoffs between competing priorities to support informed decision-making
- Identifies acceptable risk thresholds to guide sequencing and timing
- Produces defensible, data-backed roadmaps leadership can confidently support
Why This Matters
Minerva™ converts technical activity, risk data, and program progress into clear, meaningful insight that leaders can understand, govern, and confidently support — without requiring deep technical interpretation.
How Minerva™ Operationalizes Translate
- Presents risk, progress, and priorities in plain language tailored to leadership audiences
- Delivers consistent reporting and dashboards aligned to organizational risk thresholds
- Reinforces ownership, scope, and accountability across the program
- Tracks progress over time to support continuous improvement and informed investment decisions
Value (Why It Matters)
Frameworks Without the Rigidity
By applying frameworks in this way, organizations can reflect actual operating conditions, avoid false confidence from box-checking, and demonstrate due care without unnecessary complexity.
The result is alignment without distortion — and governance that holds up under scrutiny.

Why This Model Holds Up Under Scrutiny
Whether evaluated by boards, regulators, insurers, auditors, or courts, organizations must be able to explain why decisions were made, what evidence supported them, and how risk was managed over time.
Unlike point-in-time assessments or proprietary scoring models, Minerva enables continuous measurement, objective evidence, and comparable progress over time.
This creates defensibility — not just documentation.
Our Perspective on Cyber Performance
Without them, cyber risk becomes reactive, expensive, and difficult to govern. Decisions drift, investments lose focus, and leadership confidence erodes.
When they are present, cybersecurity becomes a stabilizing force — enabling clearer decisions, stronger governance, and measurable progress over time.
A Better Way to Manage Cyber Risk
It’s about giving leaders the clarity they need to make informed, defensible decisions — and sustain improvement over time.
If you’re evaluating how to move beyond snapshots, checklists, or one-off engagements, we’re happy to walk through how this model works in practice.
Free Vendor Assessments Fall Short:
- Limited Scope: Offer only a snapshot of a specific area at a single point in time.
- Marketing-Driven: Often designed as a sales tactic rather than to deliver genuine, actionable insights.
- Vendor Bias: Typically skewed to align with the vendor’s own commercial solutions, lacking objectivity.
- More Sales: Frequently serve as a stepping stone to upsell paid services or products.
- Lack of Context: Fail to provide a comprehensive understanding of your organization’s risk landscape.
Challenges with Traditional GRC Tools:
- High Costs: Enterprise-level pricing creates a significant barrier for smaller organizations to adopt these tools.
- Compliance-Centric: Focus primarily on compliance (“Big C”) rather than governance and risk management (“little g, little r”), potentially fostering a false sense of security and exposure.
- Skill-Dependent: Effective use requires a high level of expertise, making it less accessible to those without specialized knowledge.
- Technical Focus: Designed for technical users, necessitating extra effort to translate findings into actionable insights for leadership.
- Complex Integration: Integration with existing systems can be complex and time-consuming, often requiring additional resources and expertise.
- Limited Scope: Overemphasize integration and technical controls, often overlooking the critical human element that drives most organizational risks.
Limitations of Traditional Consultants:
- High Costs: Expensive due to labor-intensive processes and utilization models.
- Not scalable: Unable to scale due to the labor based delivery model.
- Point-in-Time Focus: Deliver only a temporary snapshot, lacking ongoing visibility.
- Proprietary Scales: these models lock clients into utilizing the same vendor for future engagements if they want to measure progress over time.
- Operational Disruption: Often disrupt daily operations due to their event-driven nature.
- Self-Assessment: In the end, they are all self assessments. These just have a required interview.
- Vendor Bias: Tend to align with the consultant’s own solutions, limiting objectivity.
- Sales-Oriented: Frequently positioned to lead to further paid engagements or products.
- Lack of Comprehensive Risk Insight: Fail to provide a holistic view of your organization’s risk profile.
Perspectives On Unlocking Cyber Performance
How quickly can organizations begin seeing outcomes with Minerva?
Organizations typically gain meaningful visibility and actionable insights within days of using Minerva. Because Minerva enables assessment, consolidates evidence, and visualizes risk immediately, leaders can make better decisions faster—boosting performance based on their level of commitment.
How long is a typical implementation?
- As little as ~1 week when an organization already has recent third-party assessment results or maturity scores that can be ingested directly into the platform. In these cases, Minerva can immediately normalize the data and begin producing risk visibility and prioritization.
- Several weeks for organizations that have some documentation or partial assessments but need to establish a baseline within Minerva.
- Longer, iterative ramp-up for organizations starting with little formal structure, where Minerva is used to progressively build, mature, and optimize the cyber risk program over time.
In all cases, Minerva is designed to support continuous use and improvement, delivering measurable value throughout the enablement process itself—not just at completion—while enabling sustained, risk-led decision-making as your program evolves.
Why is visibility the “key” to improving cybersecurity posture?
How does understanding risk improve organizational performance?
What role does alignment play in reducing organizational risk?
Alignment ensures every team works toward the same security objectives by clarifying ownership, roles, and workflows. This unity transforms scattered efforts into targeted execution, enabling the entire organization to operate as a coordinated risk reduction force instead of siloed departments.
How does prioritization create a competitive edge?
Prioritization channels resources toward the highest-impact risks, giving organizations a sharper focus and better results with less effort. Instead of spreading resources thin, prioritization shows exactly where investment produces the strongest risk reduction and operational benefits—unlocking strategic focus.
Why is translating cyber complexity into simple insights essential for leadership?
Leaders make faster, more confident decisions when technical data is translated into clear, actionable insight. Reporting that uses a common language empowers executives, boards, and cross-functional teams to support cybersecurity initiatives and drive organization-wide improvement.
What happens when organizations lack visibility or alignment?
Without clarity and alignment, organizations rely on assumptions—leading to higher risk, slower decisions, and inconsistent performance.Teams operate in silos, investments are misallocated, and leadership struggles to prioritize. The right key eliminates these blind spots and empowers unified action.



